Red Team? Or EDR Bypass Team

How many critical security controls can you think of?
Like really important, dramatically raising the bar for an attacker. EDR for starters has done that, it’s not perfect, but in terms of a single solution getting deployed in an organization with minimal configuration, it has a massive impact.
Over the past decade, the difficulty of phishing has also risen dramatically. There are a couple of components at play here, but at the end of the day, many Red Teams have adopted the Assume Breach model.
It might be time to shift the Assume Breach model further right.
Let’s say you’re tasked with assessing the defense plan for an embassy. If you know that the strongest safeguard the embassy has is the compound walls, what are you going to spend your time on? Determining how to better secure the wall? Or determining what happens if the wall fails.
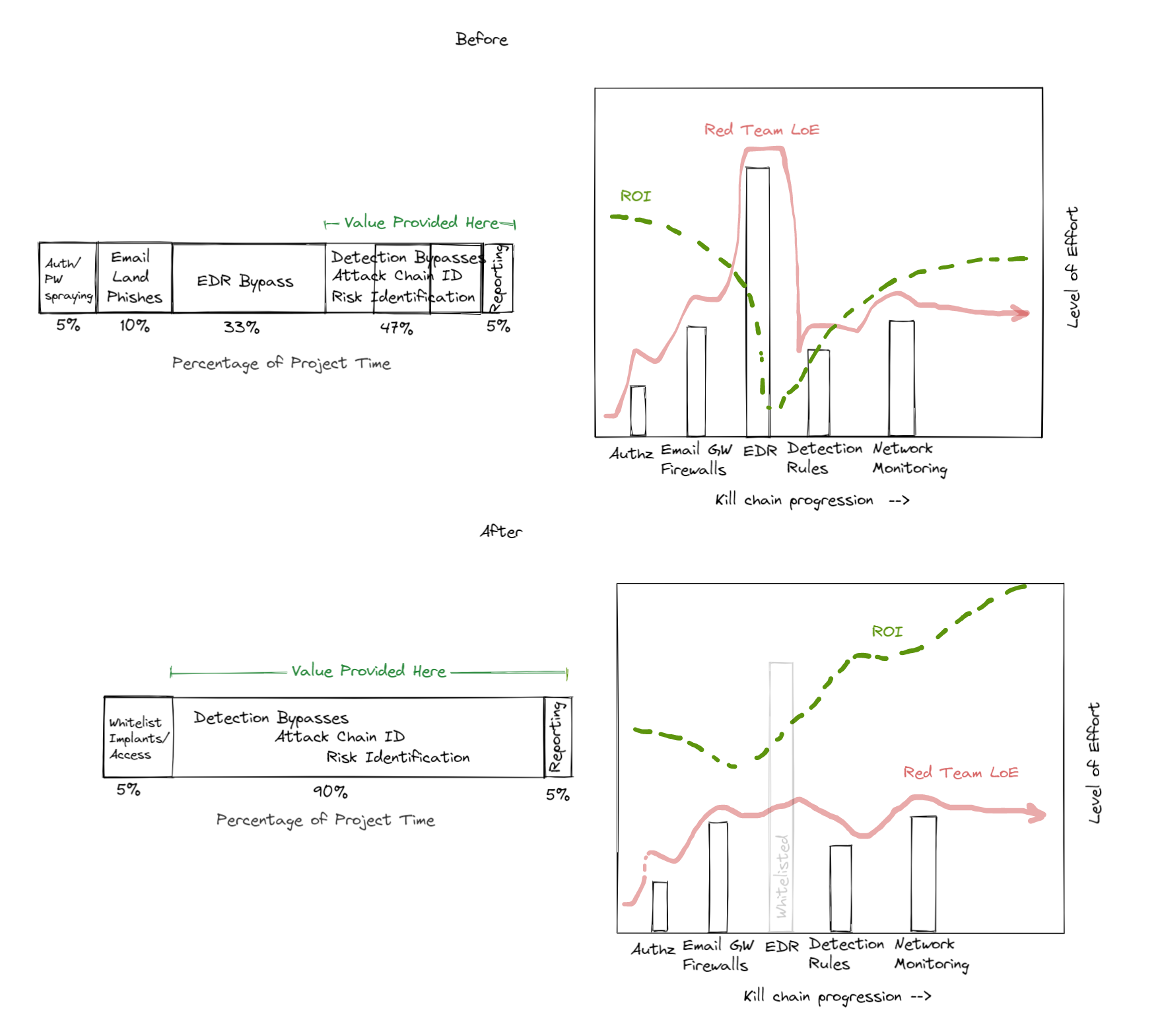
As a Red Team, spending a substantial amount of time on a single control takes away from the rest of the operation and is incredibly expensive. By skipping these controls, we acknowledge their value and are able to identify areas of improvement in other capabilities that aren’t providing the value we’d expect.
By not giving yourself strategic advantages, you may be focusing too much energy on a select group of controls, which in turn creates a bias for said controls creating an illusion of security and a reliance on a subset of the overall security stack.
So much of what makes industry waves is EDR bypass techniques, oftentimes incorporated into APT or ransomware tooling and vice versa. This is a testament to the value provided by these tools. Just because they can be bypassed (and they certainly can), doesn't mean they don't provide tremendous value or slow an attacker down significantly.
A significant portion of Red Teaming time and resources are spent bypassing EDR, either in time or tools, which reduces the time available for answering how an attacker can achieve their goals once access is obtained.
But we’re supposed to be testing the blue team!
Fire drills are still valuable even though everyone knows it's a drill. In fact, I’m not sure anyone would appreciate it if, for every fire drill, smoke was deployed to create the illusion of fire.
A Different Approach?
Creating whitelisted implants and using white carded access also creates a partnership between the Red and Blue teams. There are no egos involved, everyone is aware of what is going on and the Red Team is no longer “making the Blue Team look bad”. In fact, the Blue Team unlocked the front door and rolled the rug out.