Risk Hunting

For the sake of this article, let's use the dictionary definition of risk.
Objective-based Risk Hunt
This is the most common sort of risk hunt. This is the process of hunting for risk as part of a larger exercise, such as a red team engagement or a penetration test. In a penetration test, the risk is identified using a framework, and all risks are ideally identified in a given scope. Alternatively, in a Red Team engagement, risks that will directly aid a single desired attack path are identified.
Hypothesis-based Risk Hunt
With hypothesis-based risk hunting, a risk hunter makes a hypothesis that risk exists somewhere. The hunter then performs the risk hunt, attempting to enumerate the suspected risk.
An example is a risk hunter who makes a hypothesis that a cloud platform is leaking sensitive data through misconfigurations. The risk hunter performs the hunt by gathering details, enumerating the target, and determining if the risk exists.
Depending on the time allotted for the risk hunt, the hypothesis can be very large in scope, or very small.
Intel-based Risk Hunt
Intel-based risk hunting is the process of leveraging threat intel to drive the hunt. As with threat hunting, this type of risk hunt uses IOCs and TTPs to determine where risk may lie, or where a certain attacker will leverage a potential risk.
An example of this is when widespread vulnerabilities are released and actively exploited such as Log4Shell. An intel-based risk hunt may attempt to determine if this condition exists in the environment.
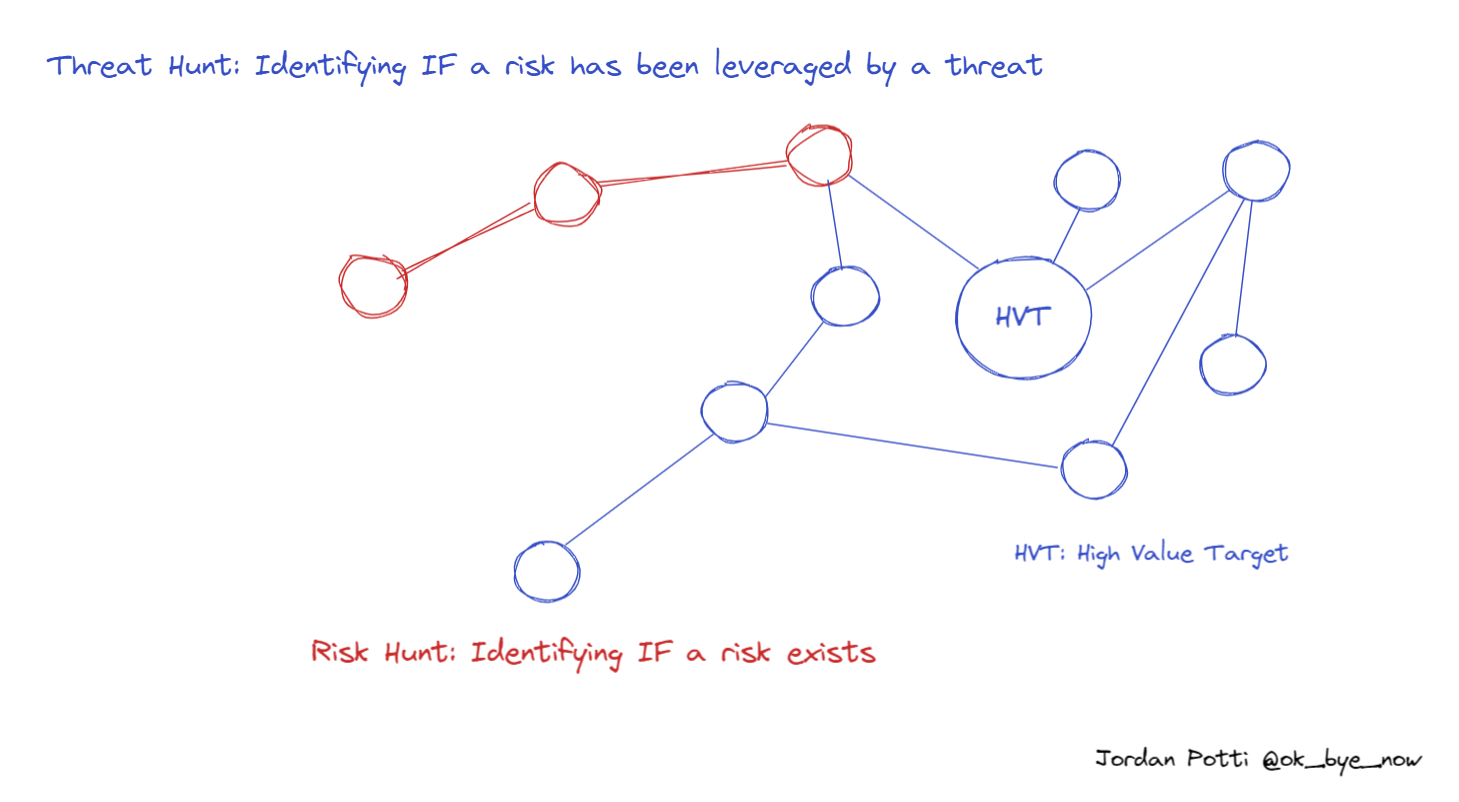
Overlap With Threat Hunting
There may be situations where a risk hunt and threat hunt are performed simultaneously. However, a risk hunt is a proactive approach, identifying risk ideally before a threat leverages the risk.
Post Hunt
All risk hunts should be documented with the time, actions performed, hypothesis, and the results of the risk hunt.
It should be expected that the hypothesis will turn out to be unverified in some cases. Ruling the hypothesis false should be reserved for cases of a comprehensive risk hunt. Ruling the hypothesis true should lead to an awareness of the risk and risk acceptance or remediation.